Free Wordlist For Wpa Crack
Distributed WPA cracking There is no dedicated resource on this machine for handshake cracking. All the work is done from volunteers like you, who contribute CPU/GPU to the cracking process by running helpcrack.py CHANGELOG , a script that will automatically fetch uncracked handshake, download wordlist, try to crack, and upload the results. Dec 09, 2016 For cracking passwords, you might have two choices 1. Dictionary Attack 2. Brute Force Attack. The Dictionary attack is much faster then as compared to Brute Force Attack. (There is another method named as “Rainbow table”, it is similar to Dictionary attack). In order to achieve success in a dictionary attack, we need a maximum size. Cracking a WPA or WPA2 network is different from cracking WEP—which means it will not just crack in a matter of minutes. Instead, you need to capture a connection handshake from a valid user that connects to the WPA or WPA2 network and then Brute force his connection with authority. May 02, 2020 In the first step, you need to download using git clone git clone Then choose a wordlist you want to use cd wpa2-wordlists/Wordlists/Crackdown2016 Then decompress (if applicable) gunzip.gz Finally, merge all text files into one using the below. If you are looking to learn Wi-Fi password hacking, this newly discovered flaw in WPA/WPA2 protocol will surely help you out. Wifi password hacking has become popular as people are always in search of the free internet. But due to the advancement of technology, hacking wifi, and cracking passwords have become a difficult task to do.
Trkiyenin lk Cracking Forum Sitesi ve Gncel Premium Account Paylamnn Tek Adresi. Quite often, the password can be guessed combining with the actual situation, scene and environment. For example for router, the first one we should think of is its. Hacking Articles is a very interesting blog about information security, penetration testing and vulnerability assessment managed by Raj Chandel. In this blog its. Ek5vSexYA/U5fqJRniT-I/AAAAAAAAAzg/s31kNVrzeMc/s1600/11.png' alt='Wpa-Wpa2 Cracking Wordlist' />We list the Top Ten Hacker Tools of 2017. Tools include Wireshark, Maltego, Aircrackng, Metasploit, John The Ripper and more Learn how to use these tools. WLHkhifkfxs/hqdefault.jpg' alt='Wpa-Wpa2 Cracking Wordlist' />Hacker Tools Top Ten List of 2. Nmap, Wireshark, Metasploit, Nessus. Nmap Network MapperUsed to Scan Ports and Map Networks and a whole bunch more Cost of Tool Free. Ks3tBY/0.jpg' alt='Wpa-Wpa2 Cracking Wordlist' />Nmap is an abbreviation of Network Mapper, and its very well known free open source hackers tool. Nmap is mainly used for network discovery and security auditing. Literally, thousands of system admins all around the world will use nmap for network inventory, check for open ports, manage service upgrade schedules, and monitor host or service uptime. Nmap, as a tool uses raw IP packets in creative ways to determine what hosts are available on the network, what services application name and version those hosts are providing information about, what operating systems fingerprinting and what type and version of packet filters firewalls are being used by the target. There are dozens of benefits of using nmap, one of which is that fact that the admin user is able to determine whether the network and associated nodes need patching. Siph0n exploits and leaks database. Recent News BTC Donations Wallet 1MwSgdmdtv8ag8x2FS1VR42cs6jCKx1Rte. Pro WPA search is the most comprehensive wordlist search we can offer including 910 digits and 8 HEX uppercase and lowercase keyspaces. Please note our Pro WPA. Nmaps been featured in literally every hacker movie out there, not least the recent Mr. Robot series. Its also worth mentioning that theres a GUI version of Nmap called Zenmap. Wed advise you to learn using Nmap i. Zenmap when you are feeling all confident. Tutorial on Hacking With Kali Linux. Anya Thailand Holiday'>Anya Thailand Holiday. Things get tough now. If you have no previous experience with Linux and virtual machines and all that stuff, getting Kali Linux up and running wont be a piece of cake. You have 2 options 3 options 1. Read the Kali official documentation That will give you an idea about what is a virtual machine, how OS can be run from USB, and how to create a partition and run 2 OS simultaneously. This is what I recommend. For that, go to Kali Official Documentation . Read my modified version of Kali documentation. The second option is to look at these posts, which are just sparingly modified and now outdated versions of the Kali docs, and offer no advantage other than saving your time as their documentations cover much more than what the ones here do, and you dont really need to know all so much. Now hacking WPAWPA2 is a very tedious job in most cases. A dictionary attack may take days, and still might not succeed. Also, good dictionaries are huge. With Kali Linux, hacking becomes much easier since you have all the tools youll ever need. This tutorial will get you started on your journey of hacking with Kali Linux. P-KtSUqzQ/U93bjlr5SxI/AAAAAAAABEk/tOAF19UhN2g/s1600/3.png' alt='Wpa-Wpa2 Cracking Wordlist' />Im linking them up here 3. Utilize the zillions of tutorials on You. Tube New optionThe time this guide was written for the first time in 2. Supreme Commander 2 Maps'>Supreme Commander 2 Maps. Kali wasnt so popular. However, now there are plenty of websites dedicated to Kali Linux, and a lot of You. Tube videos on how to install Kali. My installation guides are outdated mine are for Kali 1. Kali 2. 0 is outdated and Kali rolling is what most of you should be using. While you can use an old installation guide and make a few changes and have it work for you, its better, especially if its your first time installing an operating system alongside another, that you follow a guide tailored for your situation eg. Kali rolling on Windows 1. Kali 2. 0 on Windows 8 on Vmware. Installing an OS is serious business, dont take it lightly, and dont get discouraged if you fail at first. Also, backup your data if youre going for a dual boot. Command Line Interface. Now, if you are really sure about becoming a hacker, you have to get used to linux, and specifically the command line interface. It is often compared to and rightly so to command prompt of Windows, but Linux cli is much efficient and better than command prompt. What you have to do is do all the usual tasks you do in Windows in cli of Linux. Use cd to navigate, poweroff to shutdown, etc. Going through the complete site is on its own enough exercise to keep you occupied for a month, but you can proceed gradually. The first few tutorials here will keep in mind that you dont have much info about cli, and will be really beginner friendly. PS Tapping lt tab while typing makes Kali complete the word for you. Double tapping lt tab makes it display all possible words starting with the incomplete word. Ctrlc stops the functioning of any tool that is running. Ff Tisa Web Pro. Pressing the up arrow key shows the command you last typed.
How To Crack WPA/WPA2 With HashCat
The tutorial will illustrate how to install and configure HashCat on a Windows client and crack the captured PMKID or .hccap files using a wordlist dictionary attack.

“Hashcat is the self-proclaimed world’s fastest password recovery tool. It had a proprietary code base until 2015, but is now released as free software. Versions are available for Linux, OS X, and Windows and can come in CPU-based or GPU-based variants.”
The WPA2 handshake can be captured on a Linux compatible client like Kali Linux with a supported WiFi card running on VirtualBox. Then converted to the right format depending on the captured method and moved over to the Windows client to be cracked.
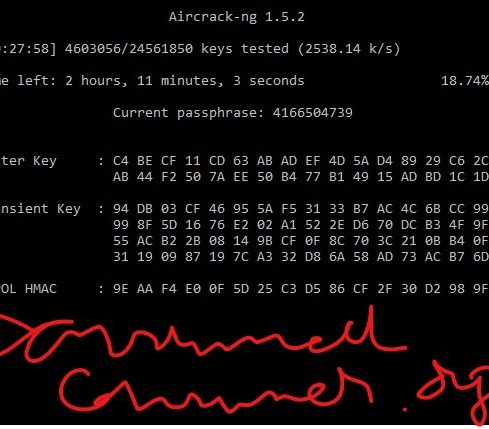

Use the guides Capturing WPA2 and Capturing WPA2 PMKID to capture the WPA2 handshake. For this test we will use the famous “Rockyou” wordlist.
DISCLAIMER: This software/tutorial is for educational purposes only. It should not be used for illegal activity. The author is not responsible for its use or the users action.

Step 1: Download HashCat
Hashcat do not require any installation, it is a portable program it requires you to unpack the downloaded archive.
- First you need to download Hashcat binaries from https://hashcat.net/hashcat/
- Navigate to the location where you saved the downloaded file, and unzip the file
Step 2: Download Wordlist
They are numerous wordlists out on the web, for this test we are going to use the famous “rockyou”.
- Open the hashcat folder on your harddrive and create a new folder called “wordlist”
- Download therockyou.txt wordlist from this Link.
- Save the downloaded file in the new folder“wordlist”
Step 3: Prepare Your Captured WPA2 Handshake
Depending on the method you used to capture the handshake you either must format the cap file to 2500 hash-mode or the PMKID file to hashcat 16800 hash-mode .
For how to format the files please see the guides Capturing WPA2 and Capturing WPA2 PMKID.
In this lab we are using a captured PMKID and a pcpa handshake formatted to hashcat readable format. “HonnyP01.hccapx ” and ” HonnyP02.16800″.
Free Wordlist For Wpa Crack Mac
I’m using two different home routers from D-Link and Technicolor for this experiment, both WiFi routers are owed by me.
- The “HonnyP01.hccapx” file is captured from the D-Link router.
- The ” HonnyP02.16800″ file is captured from the Technicolor router.
Step 4: Start Hashcat
You need to run hashcat in CMD or PowerShell. In this example we will use CMD to execute our commands and crack the handshake.
Open CMD and navigate to the hashcat folder.
Type hashcat64 -h to display all options
Step 5: Crack WPA2
In the First example we will illustrate how to get the password from a converted pcap file “.hccapx”.
Copy your converted file to the hashcat folder, in this example i am copying the file HonnyP01.hccapx to my hashcat folder.
Next we will start hashcat and use the wordlist rockyou, type in the parameters below in CMD.
- hashcat64 the binary
- -m 2500 the format type
- -w 3 workload-profile 3
- HonnyP01.hccapx the formatted file
- “wordlistrockyou.txt” the path to the wordlist
Hashcat will start processing the file, if you are successful the terminal will display the hash and the password.
Here we can see that hashcat was able to match the hash to a password in the wordlist, in this lab the password to the D-Link WiFi is “password”. You can chose to let the application run trough the wordlist or press “q” to quit.
You can display the cracked password with the “show” command or by running the same command again, all cracked hashes will be stored in the “hashcat.potfile” in the hashcat folder.
To display the cracked password in CDM type the command bellow.
Free Wordlist For Wpa Crack Free
In the next example we will run the same command except now we use the 16800 mode to run the dictionary attack against formatted PMKID file captured from the Technicolor router.
- hashcat64 the binary
- -m 16800 the format type
- -w 3 workload-profile 3
- HonnyP02.16800 the formatted file
- “wordlistrockyou.txt” the path to the wordlist
Here we can see that the cracked password is “adsladsl” for the Technicolor router.
Extra: Brute Force Attack And Rule based attack
You can let hashcat brute force the file with the command bellow.
Or use ruled base attack.
Conclusion
Your home or office WiFi can be hacked if you are using a weak password, as always a strong and complex password is still the best defense against an attacker.
DISCLAIMER: This software/tutorial is for educational purposes only. It should not be used for illegal activity. The author is not responsible for its use or the users action.
Aircrack Wordlist
