Privilege 15 Password 7 Crack
- Privilege 15 Password 7 Crack Key
- Privilege 15 Password 7 Crack Free
- Cisco Password 7 Decrypt
- Privilege 15 Password 7 Crack Download
Well armed with the salt and the hash, we can use exactly the same method that Cisco use to create the encrypted password, by brute force attacking the password, this might sound like a difficult piece of hacking ninja skill, but we simply use openssl on a Linux box (here I’m using CentOS 6.5), all you need is a wordlist.txt file (search the Internet). Also watch my Japan Vlog.try my 2D game on Android Market:- Color Coordinator - https://play.google.com/apps.
If you have Windows 7 operating system then you must have an admin account that needs a password to unlock the system. Then for a backup or other use, you may also setup a second user account. The main administrator account is used for controlling everything in the computer – from backups to updates to system maintenance. But what if you forget the password of the computer? You will lose control of the whole system including files, data, documents etc. What's the first thing you thought is how to remove local admin password?
Without an administrator password you will have no access to the computer and therefore, you won't be able to run any programs or edit files or write any new information into the PC.In short you will totally lose control over the system. However, all the accounts linked with a computer doesn't have administrator powers meaning if you have access to those accounts then it won't help you to install software, update drivers or any other tasks that are specifically designed for administrators. I mean you can't even install a new game. That's insanity!
But not to panic. There are too many tools that helps to recover a lost Windows administrator password on Windows 7. That way you will access your PC in almost no time. There are also many methods which are legit but requires special skills like programming etc.
Part 1: Reset Windows 7 Local Administrator Password using Command Prompt
For this method to accomplish, you will require a Windows 7 System Repair Disc. If you have already got it created, that's wonderful, but if not, which is quite plausible, create it on any other PC. But you must clear this CMD method is very difficult and error-prone, so we're not responsible for any system damages or data loss your device encounters.
To know the details, read the steps below:
Step 1. Now take the disc and boot your locked Windows 7 computer or laptop with it. In the course of action, in the installation interface, you wil see two link, just click 'Repair Your Computer'.
Step 2. You will be asked to hit randomly any particular key which will eventually take you to the 'System Recovery Options' screen. Make a quick note of the location or the drive displayed on screen where your operating system is installed presently. Then click 'Next'.
Step 3 On the next page, out of various System Recovery tools select 'Command Prompt'. Your black command line interpreter comes to your sight. Now enter the following codes, hitting 'Enter' after every single line of code.
Step 3. Replace the Y: with your actual operating system location which you had noted down a while ago.
It should be like this:
Step 5. After you are done with command, then eject the disc and restart your computer.
Step 6. Now when the usual blue sign-in screen rolls in, click on 'Ease of Access' icon from the bottom left corner of the screen and another cmd black dialogue box will pop up.
Step 7. On its appearance, type
Locked account name: You can type any a new account name to replacing username with your current username. You can clearly find it on the screen.
New Password: Type a new password to replace your old password.
Don't be afraid to get it wrong, just hope it work and follow as we said. If you get a errors messages pop up, don't worry, just type in the same commands again..
And that's it. You can now sign in your previously locked account with the newly created password.
For Windows 10 users: How to Reset Windows 10 Local Admin Password using Command Prompt
Part 2: Reset Administrator Password Windows 7 without Admin Rights
Though the previous Command Prompt method could reset Windows 7 local admin password hashes but it was very complicated for those users who are not used to command line interpreters. Thus iSeePassword Windows Password Recovery Pro is the easiest approach of all which instead of recovering passwords, bypasses the login screen altogether for unprotected entry, so that you can reset the password later on as per your requirement.The tool has an affinity toward every Windows OS version; File systems; Hard disks, and all type of system accounts, including guest, root, and domain along with the admin accounts. Without much effort or knowledge of how it works, just remember that it only need 3 step: Download, Burn and Reset.
iSeePassword - Windows Password Recovery Pro
- Reset local administrator, login, guest and other user account passwords on Windows OS.
- Two ways to create bootable reset disk with CD/DVD or USB flash drive.
- Fully support all computer brands: Dell, Hp, Sony, Toshiba, Acer, Samsung and ThinkPad, etc.
- Support Windows 10, 8.1, 8, 7, Vista, XP, 2000, etc. and Windows server.
What You Need:
1) A blank DVD/CD or blank USB flash drive with no less then 1G capacity.
2) An accessible Windows computer.
3) A password reset tool, directly download it below.
Firstly arrange another working computer and download the tool to it. With proper installation, run the tool with admin rights.
As you can see that you can create a bootable disk with either USB or CD/DVD. Just insert it to your computer and program will automatically recognize your USB flash drive and shows its name, then click 'Burn USB' button to start to making a reset disk. And finish the process by clicking 'Ok' button upon getting the notification 'Burning Successfully!' Here we will take USB as an example to explain how it works.
NOTE: After the burning process is finished, take out of your USB drive and insert it to your locked Win 7 PC.
Insert your newly created USB drive to your locked PC and make your PC boot from the bootable disk you just created. To do this, Just reboot your computer and press the Del or F2, or F8 or F11 based on your computer. Then go go the BIOS boot option and change the USB drive as the first boot preference order on BIOS settings page.
The program will be loaded and turns up the screen with the list of registered accounts. You just need to select your account and click 'Reset Password' and 'Reboot' option to begin the resetting of password.
After admin password resetting is done, the computer will get a drift of restart and you will enter your locked admin account without any password domination.
Part 3: Remove Windows 7 Local Administrator Password from Safe Mode
Safe mode in Windows only enables the essential programs and services while booting, subsiding the unnecessary ones. This way it helps you to fix problems like in the case of troubleshooting. Now we will use the safe mode in conjunction with command prompt to reset the forgotten Windows 7 admin password. To know the details, read the method in steps below:
Step 1. Switch on your Windows 7 laptop or home PC and before the sign in page comes to sight, press F8.
Step 2. On the next page that ensues, click on 'Safe Mode with Command prompt' and go for it.
Step 3. Instantly the little black operating Window of cmd will come up, and you have got to enter the command lines 'net user' space 'locked user account' space 'new password' and hit 'Enter'.
Now you are good to go. Your system will be restarted in a second and on the login screen this time, enter the newly created password, and you will get clear entry.
As a matter of fact all the three methods are equally applicable, but you need to stick to any one of them. Trying out all of them might be too much for your computer to handle. But if you wish to get a fully guaranteed output, then Windows Password Recovery Tool will be the best option to heed. Now the rest of the choice depends upon you.
Last week we looked at options for configuring privilege levels in Cisco IOS devices. I mentioned that there are three primary methods for doing this. The first method, which we focused on last week, was using the enable command. This article is going to look at a method that is slightly more functional in an environment with multiple administrators logging in to IOS devices. This method will expand on our understand of the local user database and will place users in the appropriate privilege level based on their assignment.
Using the local user database for authentication is easy. There is no need for “aaa new-model” or the complexity that brings along. Before we get into privilege levels, let’s first look at a router configured for local user authentication.
R1 Configuration

At this point, a user connecting to the device is prompted for a “username” as opposed to simply being asked for a password. Nothing else has really changed. The user will still be placed into privilege level 1 and will need to use the enable command to gain access to more destructive commands. To demonstrate this, we can telnet into the device.
Testing from TestPC
At this point, adding privilege levels to our users is quite simple. To demonstrate, let’s configure two additional user accounts to represent privilege level 7 and 15 respectively.
Adding Users with Privilege Levels

At this point our entire configuration, as relevant to this article, contains the following.
In order to test the two new privilege levels, we can simply login to the device through telnet, console or aux.
Privilege 15 Password 7 Crack Free
Testing User Privilege Level
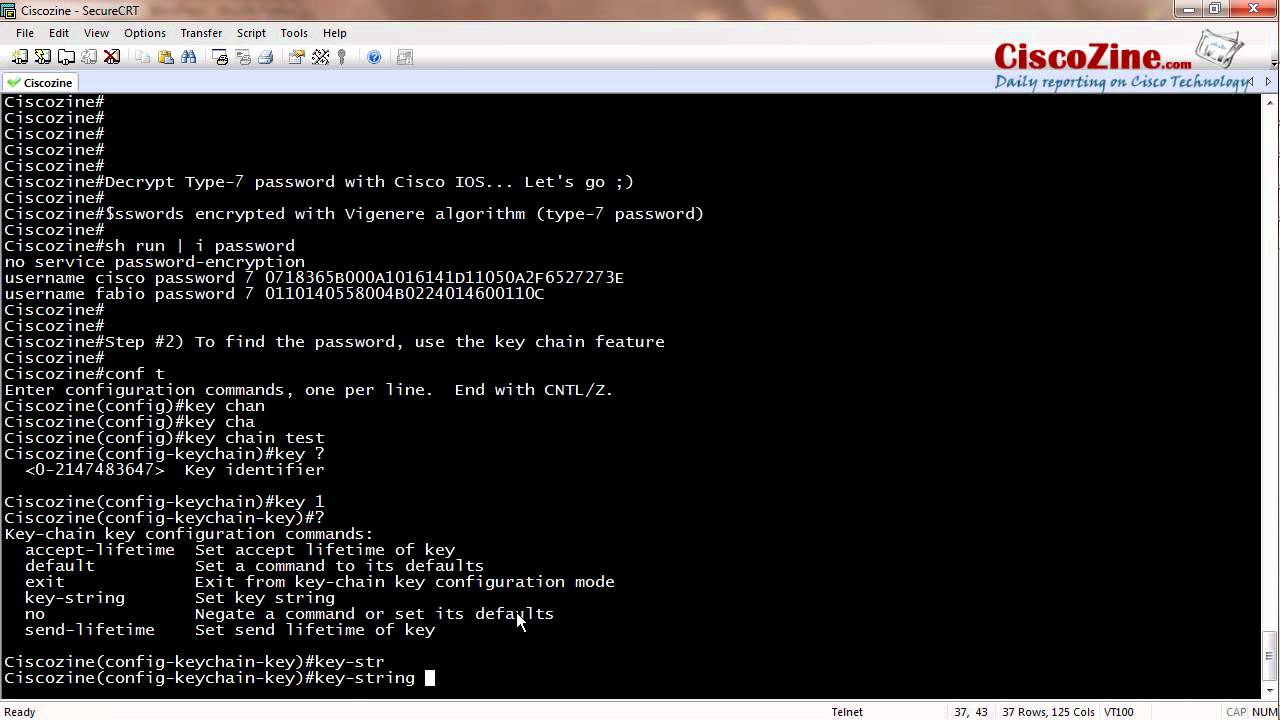
Cisco Password 7 Decrypt
As can be seen in the test, the users are immediately placed into the appropriate privilege level. The user having access to privilege level 7, would be able to access commands that are at privilege level 7 or below. The user at privilege level 15 would have access to everything. If there is no need to change the privilege level after authenticating, the enable command is unnecessary.

Privilege 15 Password 7 Crack Download
It is worth noting that commands are only at levels 0, 1 and 15 by default. Therefore, cisco and cisco7 have the same access unless the command privilege levels have been changed. Next week we will bring command privilege level into the discussion and the real world applicability of privilege levels will become apparent.
